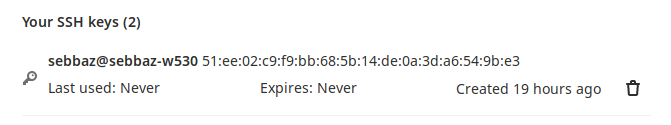
Bonjour,
Je viens demander de l’aide après avoir perdu une journée entière avec mon problème. Je m’en remets à vous.
$ ssh -Tv git@framagit.org
me demande
git@framagit.org's password
que je ne connais évidement pas…
J’ai suivit tous les tuto de la terre (français et anglais), en commençant par https://docs.framasoft.org/fr/gitlab/3-installation-poste.html (qui a très bien fonctionné sur mon poste de travail fixe à l’époque mais aujourd’hui, je suis sur un portable chez moi) mais je ne trouve pas la solution.
J’ai même créé un nouvel utilisateur sur mon ordi pour repartir à 0 mais ça n’y change rien.
j’ai fait des eval $(ssh-agent -s) et des ssh-add ~/.ssh/id_ed2559 et des ssh-add ~/.ssh/id_rs après avoir fait des ssh-keygen -t ed25519 -C "laptop-D" et des xclip -sel clip < ~/.ssh/id_ed25519.pub
ou cat .ssh/*.pub …
Quand je veux faire un git clone <copier ici l'adresse URL du projet qui est dans le presse-papier> il me mets l’erreur alors j’ai essayer de « debuger » avec un ssh -vvvT git@framagit.org
mais je ne comprends rien au résultat.
J’ai essayé de rajouter des trucs dans ~/.ssh/config mais rien n’y fait.
Je ne touche plus à rien et j’attends de voir si une bonne et compétente âme saurait m’aider.
Présentement, je n’ai plus de ~/.ssh/config ni de ~/.ssh/id_ed25519.pub ni de ~/.ssh/id_ed25519 mais seulement ~/.ssh/id_rsa et ~/.ssh/id_rsa.pub
Avez vous besoin de connaître le contenu de /etc/ssh/ssh_config ou sshd_config (je ne sais pas pourquoi j’en ai 2)?
ssh -vvvT git@framagit.org
me réponds
OpenSSH_7.6p1 Ubuntu-4ubuntu0.3, OpenSSL 1.0.2n 7 Dec 2017
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 19: Applying options for *
debug2: resolving "framagit.org" port 22
debug2: ssh_connect_direct: needpriv 0
debug1: Connecting to framagit.org [2a01:4f8:231:4c99::75] port 22.
debug1: Connection established.
debug1: identity file /home/Thatoo/.ssh/id_rsa type 0
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_rsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_dsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_dsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_ecdsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_ecdsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_ed25519 type -1
debug1: key_load_public: No such file or directory
debug1: identity file /home/Thatoo/.ssh/id_ed25519-cert type -1
debug1: Local version string SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
debug1: Remote protocol version 2.0, remote software version OpenSSH_7.9p1 Debian-10+deb10u2
debug1: match: OpenSSH_7.9p1 Debian-10+deb10u2 pat OpenSSH* compat 0x04000000
debug2: fd 3 setting O_NONBLOCK
debug1: Authenticating to framagit.org:22 as 'git'
debug3: hostkeys_foreach: reading file "/home/Thatoo/.ssh/known_hosts"
debug3: record_hostkey: found key type ECDSA in file /home/Thatoo/.ssh/known_hosts:1
debug3: load_hostkeys: loaded 1 keys from framagit.org
debug3: order_hostkeyalgs: prefer hostkeyalgs: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521
debug3: send packet: type 20
debug1: SSH2_MSG_KEXINIT sent
debug3: receive packet: type 20
debug1: SSH2_MSG_KEXINIT received
debug2: local client KEXINIT proposal
debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ext-info-c
debug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256,ssh-rsa
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com,zlib
debug2: compression stoc: none,zlib@openssh.com,zlib
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug2: peer server KEXINIT proposal
debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1
debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com
debug2: compression stoc: none,zlib@openssh.com
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug1: kex: algorithm: curve25519-sha256
debug1: kex: host key algorithm: ecdsa-sha2-nistp256
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug3: send packet: type 30
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug3: receive packet: type 31
debug1: Server host key: ecdsa-sha2-nistp256 SHA256:nO6L2sApWj/OkjW7avditV/dHOMEG/cV7Ps5z7yaS30
debug3: hostkeys_foreach: reading file "/home/Thatoo/.ssh/known_hosts"
debug3: record_hostkey: found key type ECDSA in file /home/Thatoo/.ssh/known_hosts:1
debug3: load_hostkeys: loaded 1 keys from framagit.org
debug3: hostkeys_foreach: reading file "/home/Thatoo/.ssh/known_hosts"
debug3: record_hostkey: found key type ECDSA in file /home/Thatoo/.ssh/known_hosts:2
debug3: load_hostkeys: loaded 1 keys from 2a01:4f8:231:4c99::75
debug1: Host 'framagit.org' is known and matches the ECDSA host key.
debug1: Found key in /home/Thatoo/.ssh/known_hosts:1
debug3: send packet: type 21
debug2: set_newkeys: mode 1
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug3: receive packet: type 21
debug1: SSH2_MSG_NEWKEYS received
debug2: set_newkeys: mode 0
debug1: rekey after 134217728 blocks
debug2: key: /home/Thatoo/.ssh/id_rsa (0x55efbaf9d860), agent
debug2: key: /home/Thatoo/.ssh/id_dsa ((nil))
debug2: key: /home/Thatoo/.ssh/id_ecdsa ((nil))
debug2: key: /home/Thatoo/.ssh/id_ed25519 ((nil))
debug3: send packet: type 5
debug3: receive packet: type 7
debug1: SSH2_MSG_EXT_INFO received
debug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521>
debug3: receive packet: type 6
debug2: service_accept: ssh-userauth
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug3: send packet: type 50
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,password
debug3: start over, passed a different list publickey,password
debug3: preferred gssapi-keyex,gssapi-with-mic,publickey,keyboard-interactive,password
debug3: authmethod_lookup publickey
debug3: remaining preferred: keyboard-interactive,password
debug3: authmethod_is_enabled publickey
debug1: Next authentication method: publickey
debug1: Offering public key: RSA SHA256:XKm/NTOn9tfaxAJNxBVq91dJ4zqfd0AeEtuptNt499w /home/Thatoo/.ssh/id_rsa
debug3: send_pubkey_test
debug3: send packet: type 50
debug2: we sent a publickey packet, wait for reply
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,password
debug1: Trying private key: /home/Thatoo/.ssh/id_dsa
debug3: no such identity: /home/Thatoo/.ssh/id_dsa: No such file or directory
debug1: Trying private key: /home/Thatoo/.ssh/id_ecdsa
debug3: no such identity: /home/Thatoo/.ssh/id_ecdsa: No such file or directory
debug1: Trying private key: /home/Thatoo/.ssh/id_ed25519
debug3: no such identity: /home/Thatoo/.ssh/id_ed25519: No such file or directory
debug2: we did not send a packet, disable method
debug3: authmethod_lookup password
debug3: remaining preferred: ,password
debug3: authmethod_is_enabled password
debug1: Next authentication method: password
git@framagit.org's password:
On m’a demandé de donner
$ ls -larh /home/Thatoo/.ssh/id_rsa.pub
-rw-r--r-- 1 Thatoo Thatoo 411 mars 26 16:43 /home/Thatoo/.ssh/id_rsa.pub
On m’a demandé aussi
$ ls -lrdt ~/.ssh
drwx------ 2 Thatoo Thatoo 4096 mars 26 16:50 /home/Thatoo/.ssh